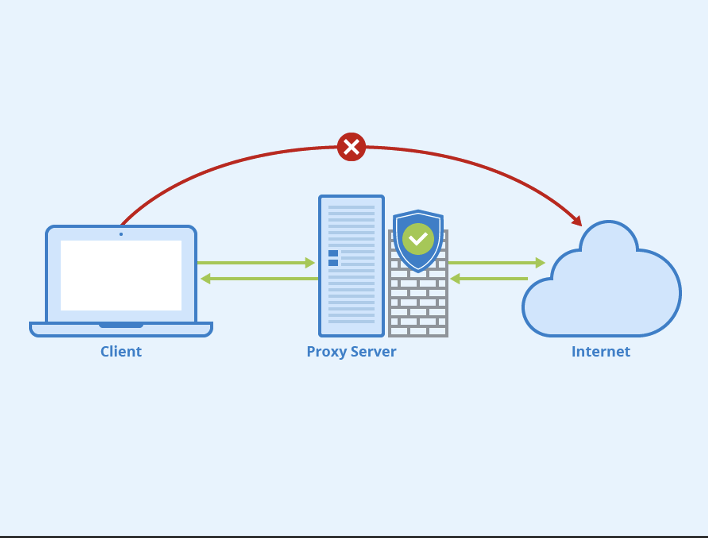
A proxy server is a computer that serves as an intermediary between your computer and the internet. The goal of using a proxy server is to filter your web traffic, which can be useful for companies concerned with data security or compliance issues. Companies use proxies because they are beneficial in many ways, such as:
Protects sensitive information:
A proxy server can prevent sensitive information from leaving the company’s network. For example, a financial institution may use a proxy to block employees’ access to social media sites and entertainment websites so that proprietary information is not leaked or shared outside of the office environment. It may also be used to protect company information that could be exposed to security breaches if accessed by unauthorized parties.
Protects business infrastructure:
A proxy server can also be used as a fail-safe measure in the event of an emergency, such as when there is damage or loss at one of your company’s data centers. With this type of setup, all web requests will automatically route through the internet connection on another site until service can be restored at the primary location. This minimizes downtime and ensures continuous uptime for both employees and customers alike. That’s the same reason why you find most torrent sites like pirate bay proxy or lime torrent using the proxy servers.
Faster load times:
If you’re using a content delivery network (CDN), then your website should run much faster than it would otherwise because CDNs cache static resources like images and videos locally. The added security is why many companies choose to use a content delivery network (CDN).
Why? Because it also prevents DDoS attacks, which are attempts by hackers to disrupt service on your web server through the use of bots that send continuous requests with spam traffic. CDNs can help prevent these types of attacks because they act as filters for your website’s data, blocking all disallowed IP addresses from accessing information hosted on their servers. This helps secure company-sensitive information like credit card numbers or trade secrets.
These proxies are particularly useful for individuals, marketers, or businesses who need to manage multiple Instagram accounts, automate actions, or access Instagram from different locations. proxy for Instagram provides several benefits, including the ability to bypass restrictions such as IP bans, access geographically restricted content, and maintain anonymity while engaging with Instagram activities. By rotating IP addresses, users can simulate different locations, enabling them to target specific regions or demographics. Instagram proxies also offer enhanced security by masking the user’s original IP, preventing potential tracking or identification.
Protects against web-borne malware:
A proxy server can block users from accessing malicious websites, which protects them and the company’s network from viruses or other harmful software that could be distributed through these sites. For example, an organization may filter out all requests for pornographic content in order to prevent employees from inadvertently downloading inappropriate materials onto their work computers. It also prevents any sensitive data stored on the user’s computer (e.g., Social Security numbers) from being transmitted across unsecured networks en route to its intended recipient.
Monitor employees’ browsing habits:
Some companies try to prevent employees from wasting time while surfing the web. For example, a company might only allow access to certain websites during lunch breaks or at times when it is convenient for supervisors and managers. It can also monitor employees’ browsing habits to see what websites they visit. The user’s connection with the proxy server can be monitored, and you might even detect malware or viruses if an employee downloads it onto their work computer (which could result in additional costs associated with fixing infected computers).
Filtering out malicious code and spam:
Another reason that companies use proxies is to filter out spam and malicious code (or malware). The basic idea behind this goal is similar: if employees are allowed access only to specific websites, it can help prevent them from clicking on links or downloading attachments in suspicious emails. This can help prevent infections from viruses or malware.
In addition, when employees visit potentially malicious sites through a proxy server, the connection between their work computer and these external sources can be monitored more closely. This allows companies to detect potential risks associated with an employee’s internet usage in real-time.
Locating unauthorized content:
Finally, some proxies are used by administrators who want to track down files they’re not supposed to have access to on company computers (or user accounts). For example, if you run a small business that makes software for PCs and someone from your team uses one of your programs at home—and then downloads it onto his personal laptop without permission—you might use a proxy server to find out what he’s accessing. The proxy server will send you a log file showing what websites were accessed or files downloaded. You can then determine whether it was appropriate for him to use the software on his personal computer and take further action if necessary.
Monitoring traffic patterns:
A final benefit of proxy servers for businesses is the ability to monitor web traffic patterns such as who has visited what website, how often, which pages were viewed within a certain time frame, etc. This information could be beneficial when trying to determine whether new content should be added to your website or if you need additional bandwidth so more people can visit at once. It’s also advantageous because some business processes may require heavy internet usage during off-hours while some may not, so you can schedule those processes to take place during your business hours rather than using up what little bandwidth might be leftover.
Conclusion:
It is evident that proxy servers are extremely beneficial for companies that have strict data compliance or security regulations.